Officially Endorsed
Wireshark Foundation
The Wireshark Certified Analyst (WCA) Complete Course
Official Wireshark Certified Analyst - The Complete Course
Backed by the Wireshark Foundation, this immersive program shows you exactly how to troubleshoot, analyze, and secure packet flows with confidence.
- Hands-on Wireshark labs that mirror real packet captures.
- Master Ethernet, ARP, IPv4/6, TCP, ICMP, and more.
- Follow a guided progression that keeps you focused and confident.
PacketSafari partners with top training providers—purchases through this link help us keep building free labs and articles.

Decoding Ethernet-in-L2TPv3

Disabling AI Assistance for PCAPs
PCAP Prompt Compression

PacketSafari PCAP Sanitization

How to Anonymize a PCAP

Capture PCAPs without Wireshark
Comparing Network Analysis Tools

How to decrypt TLS traffic in Wireshark

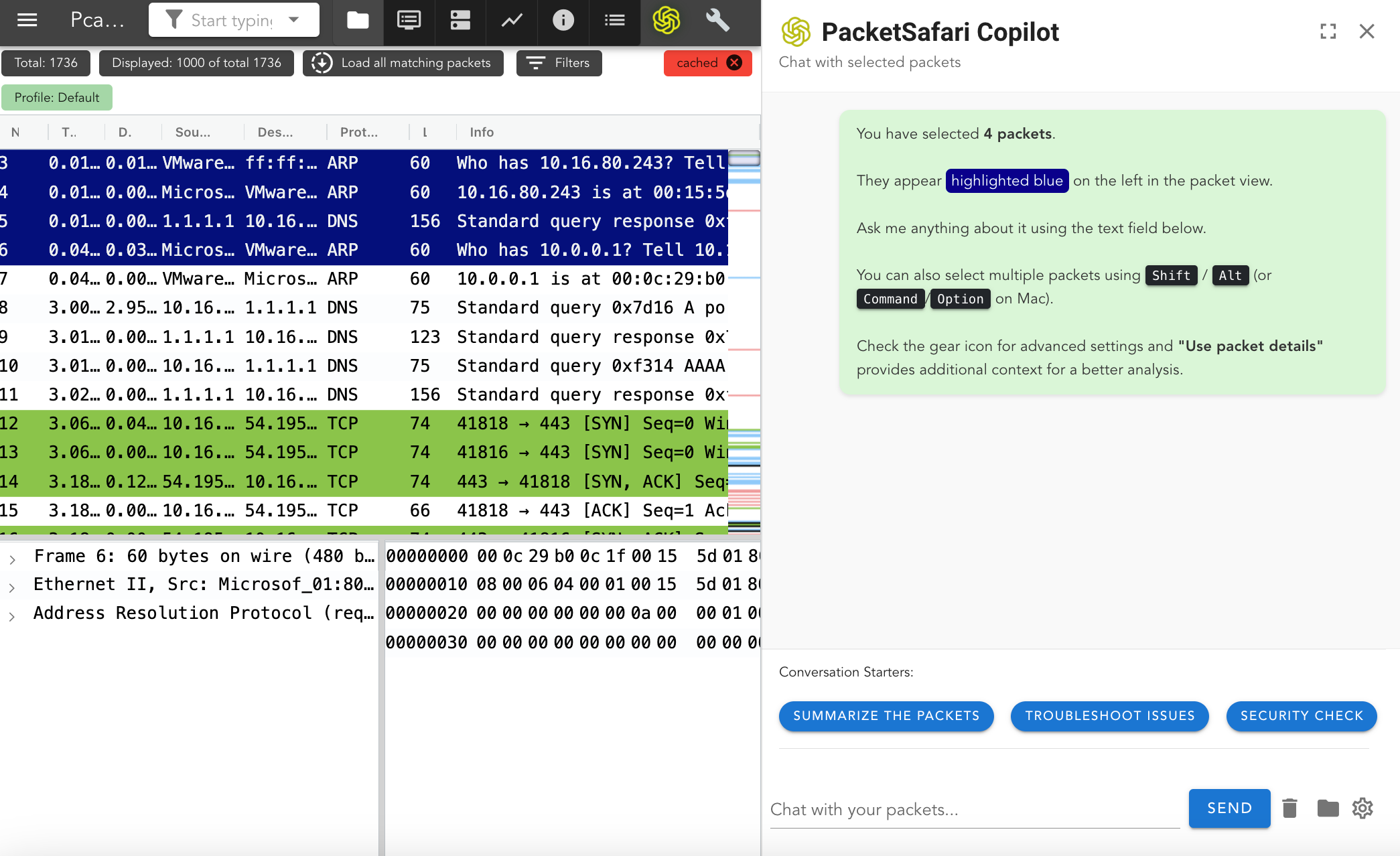
Introducing Packetsafari Copilot
Find SMBv1 using Wireshark

AI Shark

Ransomware Protection: Best Practices in Backup and Defense

NIS2 Directive: All You Need to Know

Zero Trust: Building a More Secure IT Environment

PacketSafari is looking for Sponsors

Filtering Insecure Communication in Wireshark: Uncovering Security Risks

GDPR Compliance: Everything You Need to Know

PCAP Analysis: Tips and Tricks for Effective Network Traffic Analysis

NIS2 Directive: Best Practices for Conducting Risk Assessments

The Importance of NIS2 in Protecting Against Advanced Malware Attacks

Unraveling the IPv4 Protocol: The Significance of IP IDs and the IPv4 Header Explained
The Importance of Multi-Factor Authentication for NIS2 Directive Compliance

Staying Ahead of the Curve: NIS2 and Proactive Network Monitoring

How to Analyze PCAP Files Online: A Beginner's Guide

Online Wireshark Training by the makers of the online PCAP analyzer PacketSafari

NIS2 Directive: The Importance of Incident Response Plans

RTP Voice Stream Analysis in Wireshark: Common Problems and Solutions

Investigating Network Issues with ARP: Real-World Case Studies Using PacketSafari and Wireshark

Demystifying ICMP Errors: Understanding Destination Unreachable, Fragmentation Needed, and MTU Issues

TCP Segment Loss in Wireshark: Expert Tips and Tricks

Solving TryHackMe Wireshark Filters room with PacketSafari - Part I Protocol Filters

Wi-Fi Traffic Analysis with Wireshark: 5 Case Studies You Need to Know
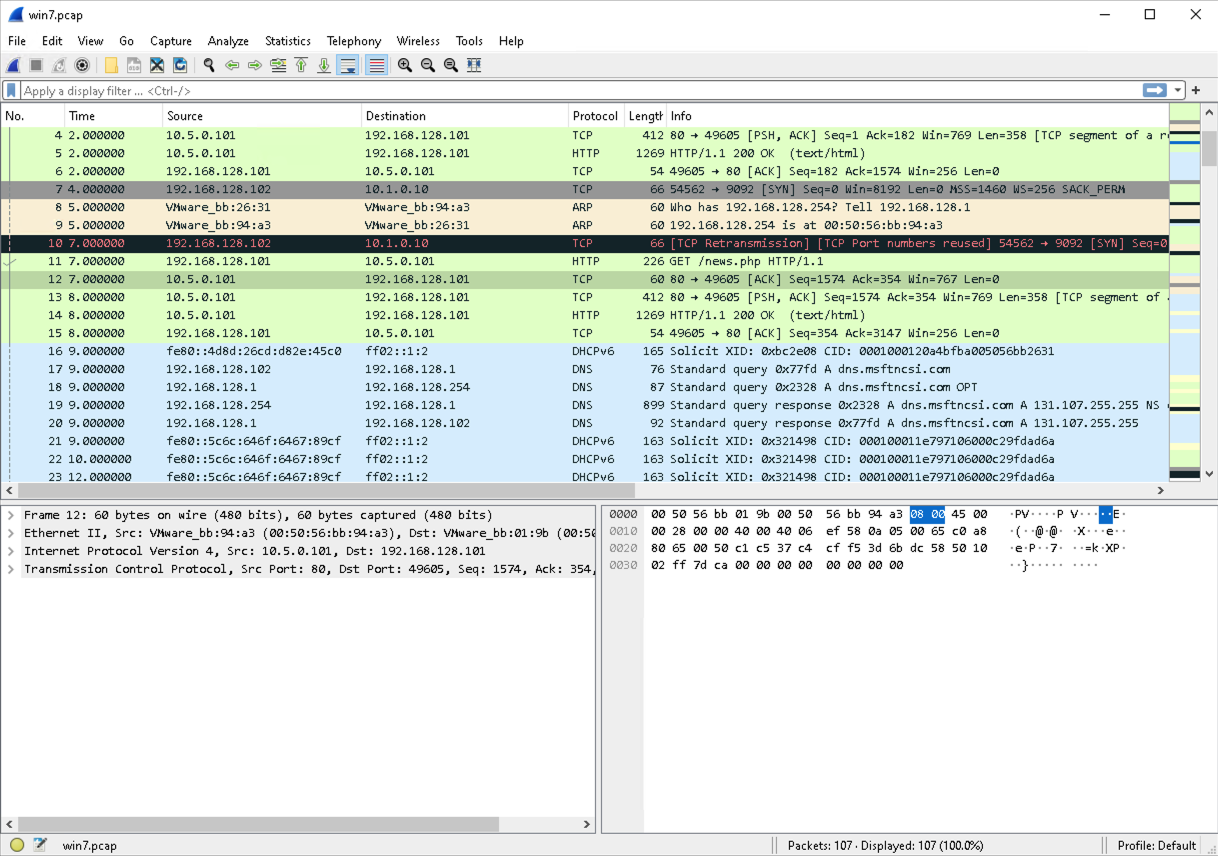
Windows name poisoning remains a dangerous attack vector
Wireshark has a new default layout

Comparing HTTP/1, HTTP/2, HTTP/3, and QUIC: Key Differences, Commonalities, Pipelining, and Multiplexing

Layer 2 and 3 Changes in First Hop Redundancy Protocols: Failover and Active-Active Mechanisms

A short Guide to DNS Protocols: DoH, DoT, DNSSec, and DNSCurve

Basics of First Hop Redundancy Protocols: Analysis and Troubleshooting with Wireshark

Unraveling DNS Mysteries: 3 Real-World Case Studies Analyzing DNS in Wireshark

How to merge Wireshark upstream changes into a local fork

GDPR, Google Analytics and leaking hashes

STP Analysis with Wireshark: 3 Real-World Case Studies

Analyzing NTP Traffic with Wireshark: A Practical Guide for Network Administrators

QoS Analysis with Wireshark: 3 Case Studies

Wireshark TCP Trace Graph Tutorial

Packet Capture Challenges in the Cloud: Case Studies and Real-World Examples

VoIP Troubleshooting: Essential SIP and RTP Case Studies for Success

Capturing Bluetooth and USB Traffic with Wireshark: Expert Guide on Installing and Using NPCAP Driver

SMBv1 vs SMBv2 vs SMBv3: Understanding the Differences and Securing Your Network

Packet Capturing on Mobile Devices: A Comprehensive Guide for iPhones and Androids

Mastering the Art of Multicast Video Traffic Analysis: 3 Real-World Troubleshooting Case Studies

Advanced Troubleshooting of Kerberos Problems with Wireshark: 5 Real-World Case Studies

Unraveling Layer 2 Problems: Expert Tips for Troubleshooting Network Issues

Link Aggregation: LAG, LACP, Etherchannel, MLAG, VSS, Stacking and FHRP