How to Anonymize a PCAP

Officially Endorsed
Wireshark Foundation
The Wireshark Certified Analyst (WCA) Complete Course
Official Wireshark Certified Analyst - The Complete Course
Backed by the Wireshark Foundation, this immersive program shows you exactly how to troubleshoot, analyze, and secure packet flows with confidence.
- Hands-on Wireshark labs that mirror real packet captures.
- Master Ethernet, ARP, IPv4/6, TCP, ICMP, and more.
- Follow a guided progression that keeps you focused and confident.
PacketSafari partners with top training providers—purchases through this link help us keep building free labs and articles.
PCAP files capture comprehensive network traffic, often including sensitive information such as personal data, credentials, and other confidential details. Anonymizing these files is essential to protect privacy, comply with data regulations, and safely share network captures without exposing critical information.
By applying techniques like packet slicing and utilizing tools such as editcap and TraceWrangler, you can remove or obscure sensitive data. This not only enhances security but also reduces file size and simplifies subsequent analysis. In this guide, we explore the methods for anonymizing PCAPs and explain why these practices are crucial before uploading files to services like PacketSafari Analyzer or Copilot.
Using editcap
Editcap is a command-line tool that comes bundled with Wireshark, the popular network protocol analyzer. Because it’s included with Wireshark, you’ll need to download and install Wireshark to use editcap. You can download Wireshark from the official website
On Windows, Wireshark is generally installed in C:\Program Files\Wireshark\. You can locate the editcap.exe file in that folder. C:\Program Files\Wireshark\editcap.exe" -s 80 input.pcap output.pcap. Make sure to use quotes around the path if it contains spaces
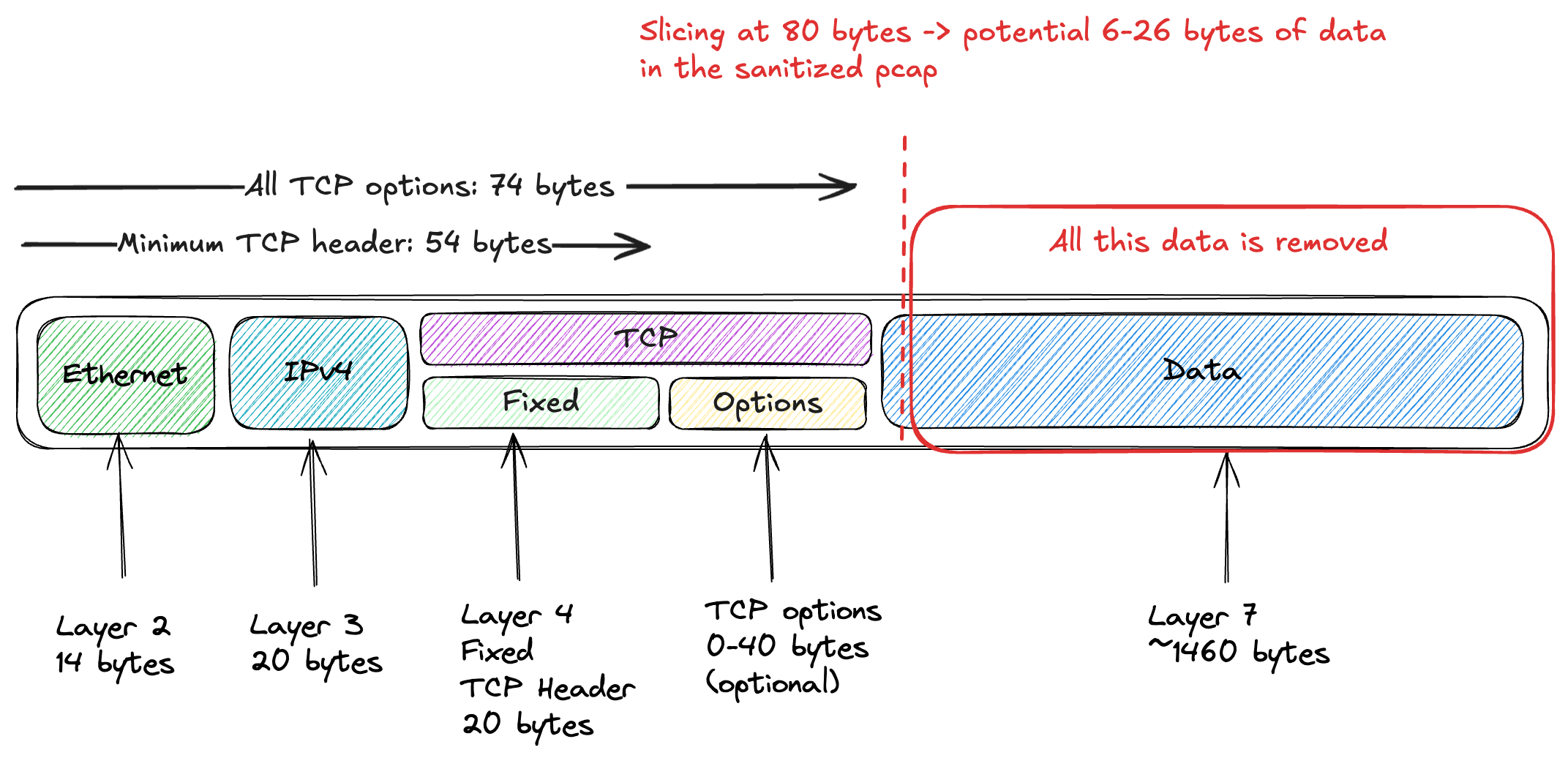
editcap allows you to sanitize your PCAP files by truncating packets after a specified byte offset. This method helps remove sensitive data contained in the packet payload. Keep in mind that the optimal offset may vary depending on the protocol, its options, tunneling, and other factors. For capturing all data up to layer 4, 80 bytes is usually sufficient. If you need to anonymize data at layer 7, it becomes more challenging.
For example, to truncate packets after 80 bytes, run:
editcap -s 80 TCP-to-Websites.pcapng TCP-to-Websites-sanitized.pcapng
Here is a diagram to give you a better idea what slicing means
In this example, two files are available on PacketSafari: Original and Anonymized. The screenshot shows the original file on the left and the anonymized version on the right, where each packet contains only the first 80 bytes.
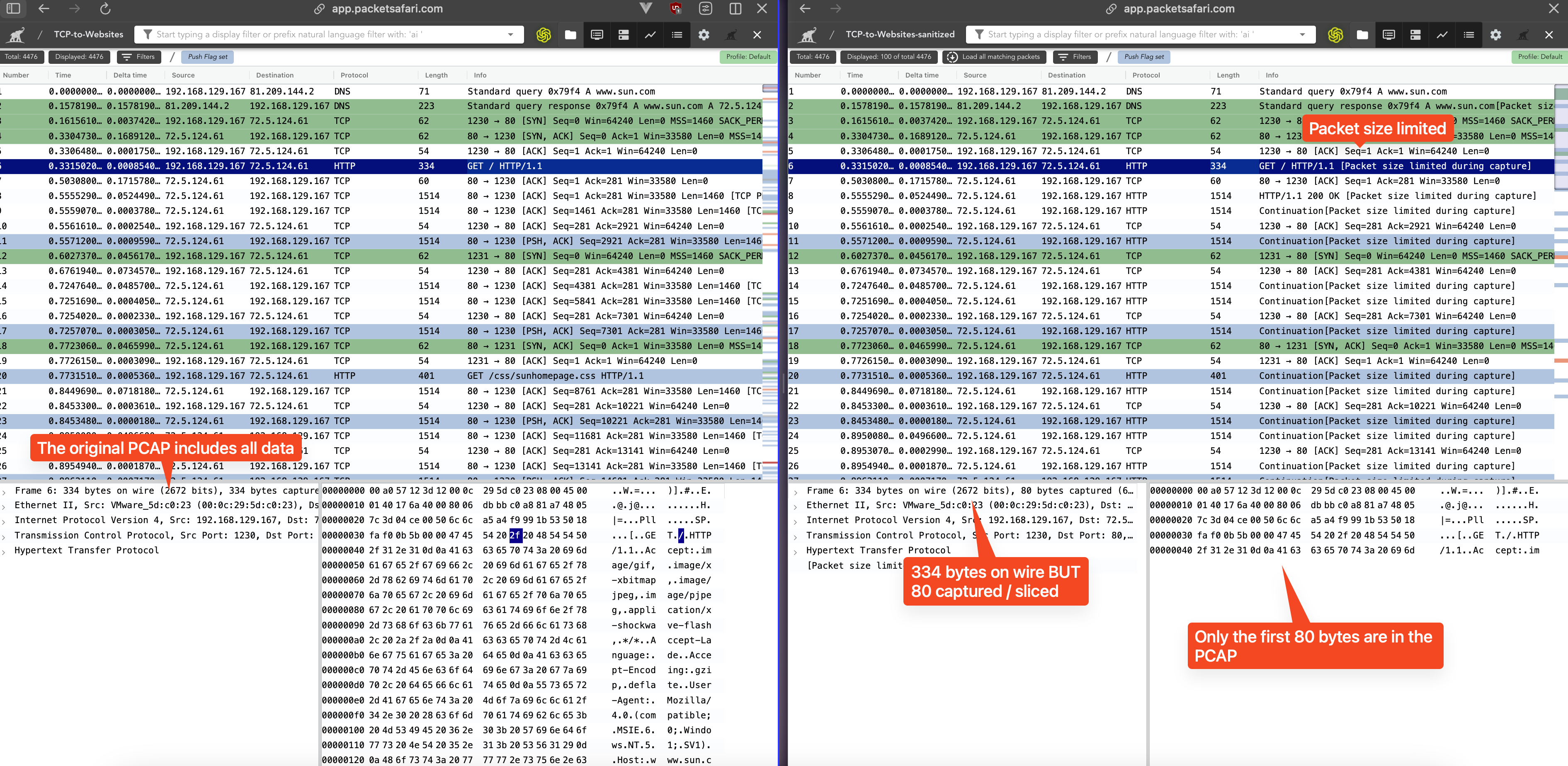
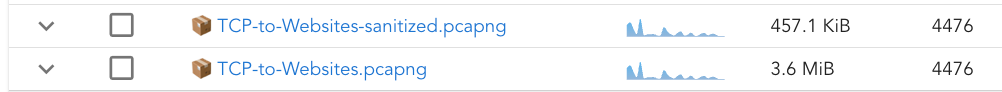
This not only sanitizes the data but also significantly reduces the file size.
Using TraceWrangler
If you need to anonymize additional details such as MAC addresses, IP addresses, and other sensitive information, a more powerful tool is required. A recommended Windows-only tool for this purpose is TraceWrangler. For further guidance, you can refer to The Wireshark Q&A Trace File Sharing Tutorial.
Chris Greer has also provided a useful video on how to use TraceWrangler, available here: Watch on YouTube
TraceWrangler can anonymize packets up to layer 4 (including UDP, TCP, ICMP, and ICMPv6). However, if your PCAP files contain sensitive data in higher layers (such as HTTP, SMTP, SMB, etc.), we recommend using packet slicing as a complementary approach.
Packet Slicing Explained
Packet slicing involves truncating packet data to remove the payload that might contain sensitive information. Instead of relying solely on anonymization tools that modify header fields, packet slicing retains only a fixed portion of each packet (typically the header), effectively discarding the rest.
Why Use Packet Slicing?
- Enhanced Data Security: By removing the payload data, you reduce the risk of exposing confidential or sensitive information.
- Reduced File Size: Sliced packets result in smaller PCAP files, making them easier to handle and faster to upload.
- Compliance and Privacy: It minimizes the amount of personal or sensitive data shared, which is important for privacy and compliance with regulations.
- Simplified Analysis: Keeping only the essential header information can be sufficient for many types of network analysis, without the noise of complete packet payloads.
Before uploading to services like PacketSafari Analyzer or Copilot, packet slicing ensures that only the necessary data is shared, thereby protecting your privacy and enhancing security without sacrificing analytical value.

