Introduction
Packet Safari makes it easy to collect, share, and analyze your network captures (PCAPs) 📦
What is network packet analysis?
Network packet analysis is the art of understanding the network protocols that power up our modern communication. Cars, aeroplanes, power plants, webshops, and maybe even toasters could not work without different devices talking to each other. Network analysis is key to understanding how this communication works, how to improve, and how to troubleshoot issues.
So why is it called packet analysis? In digital communication, it is very common to packetize the data that is to be transmitted. These packets then include information about the sender, the destination, and the priority like a parcel. This metadata is encoded in the so-called packet headers. Like an onion, there might be multiple layers of a packet header for different protocols.
Therefore a packet has a protocol stack. A very common stack today is something like Ethernet, IP, TCP, and HTTP. Packet analysis mostly is concerned with the interpretation of these protocol headers but one might also analyse the content or payload of the packets (the actual transported data like an image, voice, text). The analysis of the content is interesting for security or forensic purposes whereas header analysis mostly is useful for performance tuning, troubleshooting, and debugging.
Why is it useful?
Packet analysis has a wide variety of applications in many fields like
- 🌐 Communication providers
- 🌥️ Cloud providers
- 🛡️ Cybersecurity
- 🏥 Healthcare
- 🏫 Education
Packet analysis is useful for:
- Network troubleshooting
- Network performance analysis
- Cybersecurity analysis
- Protocol debugging and development
- Application development
- Verification of network security monitoring (IDS/IPS/NG Firewall) alerts
- Network forensics
- Metadata analysis
Why Packet Safari?
Packet Safari is a repository of network packet captures and is powered by a web-based protocol analyzer.
- Web Frontend - Analyze and share trace files without any tool installation.
- Trace archive - Access central PCAP archive and samples.
- Web enriched PCAPs - Trace information is enriched with web-based data.
- Comments - Traces can be commented.
- Tagging - Easily organize your trace files using tags.
- Permissions - Share PCAPs with your team or if you are a teacher with students.
- Graphing - Graph PCAP data.
- Indexing - Index arbitrary protocol fields.
- Advanced querying - Advanced querying within a PCAP supporting aggregations.
- Multi PCAP search - Search arbitrary protocol fields across multiple PCAPs.
- TCP Steam queries - "find all connections that transfer a certain file"
- Mass actions - Mass tagging, delete, permissions.
- Coloring rules - Coloring of packets.
- Context menus - Context menus on packet, decode and hex view level.
How it works
Uploaded packet traces can be organized, tagged, searched and shared with different people so that everybody has access to the same analyses.
1. Explore Public PCAPs
From the top left corner, you can open the navigation menu. There you can open the PCAP browser to explore public PCAPs.
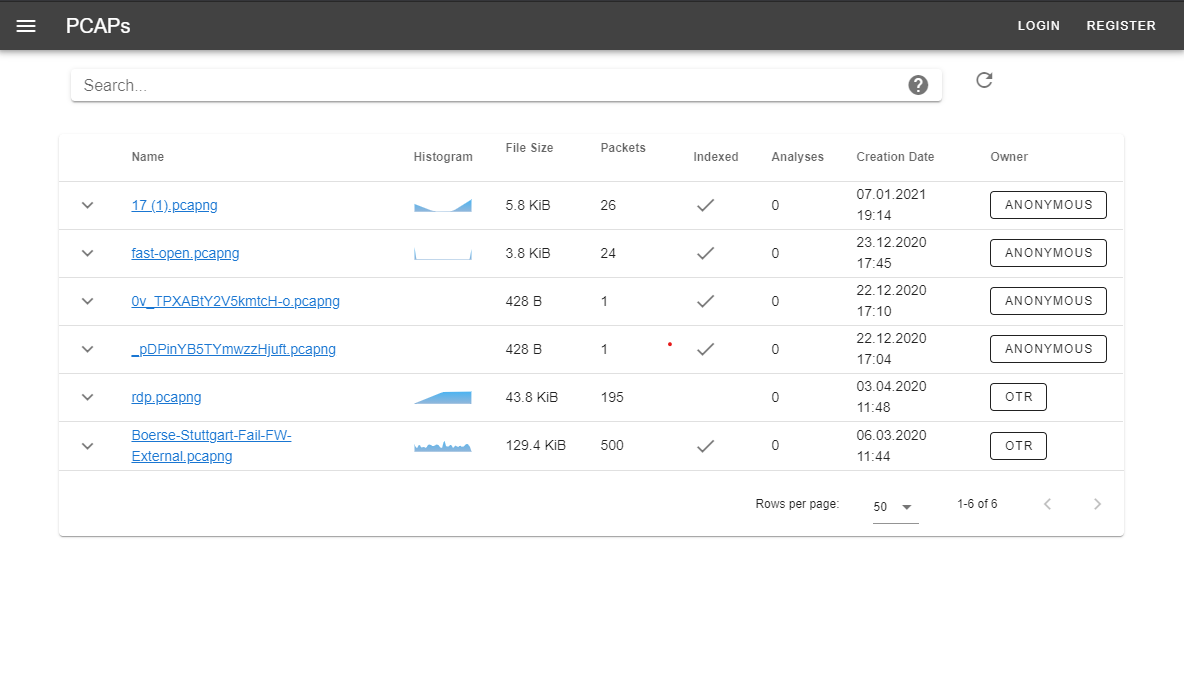
2. Browse PCAPs
Full Experience
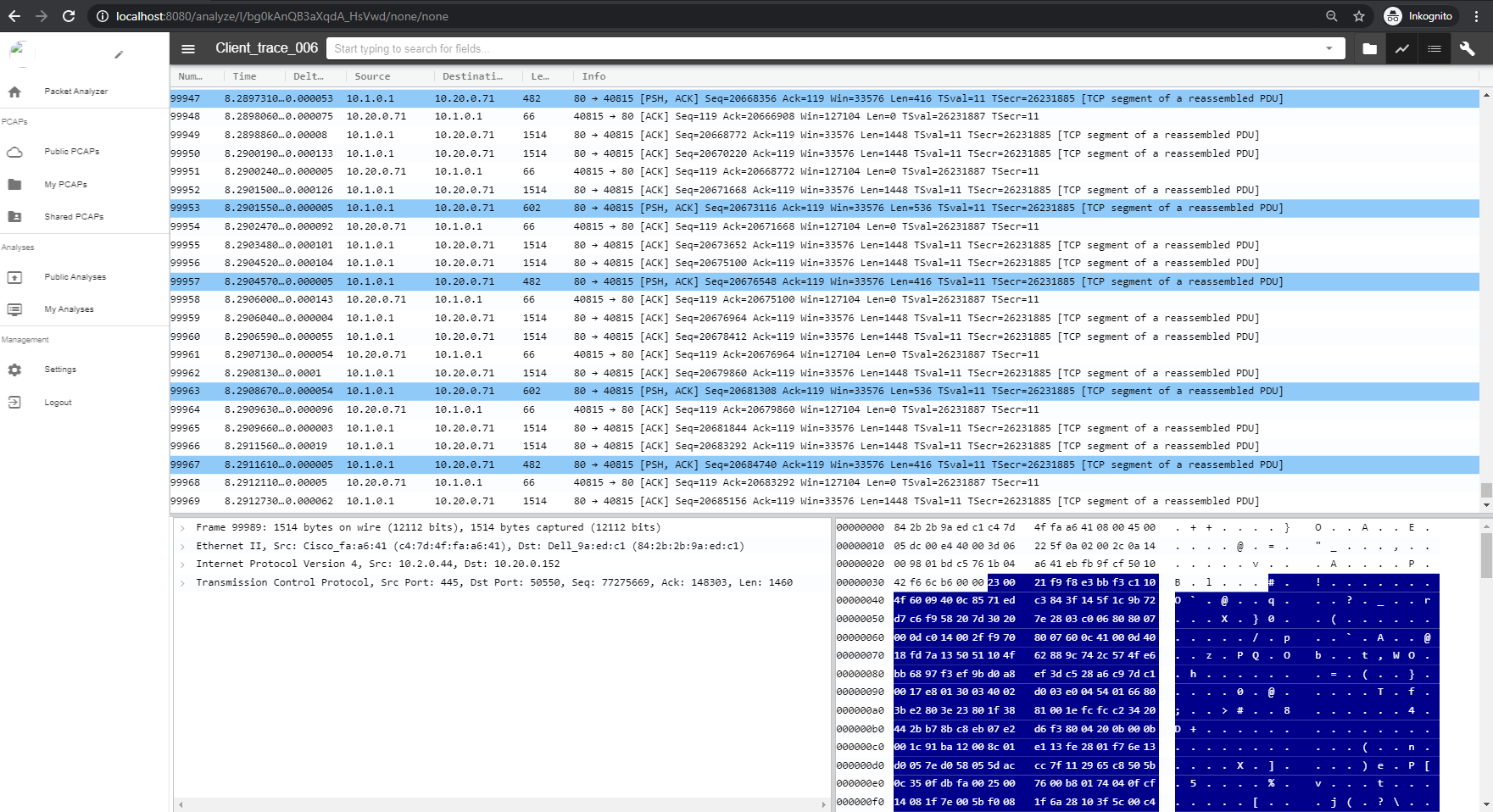
Contribute
1. Upload a trace file
When you upload a trace to Packet Safari it does some automatic processing on that file...
- You can upload
.pcapand.pcapngfiles
2. View the trace file
You can access the trace via an URL and share that URL with others. You can also restrict access to the file.
3. Next steps
- Explore some of the features of the UI
- Explore sample trace files of others
Alternatives
- Wireshark. The mother of all packet analysis tools.
- Cloudshark A cloud-based packet analysis tool.
- Trace Wrangler Mass trace processing.
