Decryption
⚡️ Packet Safari can display decrypted packets
To decrypt a PCAP with Packet Safari you need to have an SSLKEYLOGFILE. This file can be created in a variety of ways depending on what device you control. You need to configure to log encryption keys to a SSLKEYLOGFILE before you start capturing the network traffic or you won't be able to decrypt the captured traffic.
Once you have both the PCAP and the SSLKEYLOGFILE you can upload both files and Packet Safari will create a new file that merges these two files into one new decrypted file.
SSLKEYLOGFILE
Set the SSLKEYLOGFILE environment variable either globally or just start your application from a terminal.
It is supported by Firefox, Chrome, Curl, mitmproxy, Exim,
Windows
Windows CMD
C:\> set SSLKEYLOGFILE=%USERPROFILE%/Desktop/sslkeylog.log
C:\> echo %SSLKEYLOGFILE%
Windows PowerShell
PS C:\> $env:SSLKEYLOGFILE = "$env:USERPROFILE\sslkeylog.txt"
PS C:\> $env:SSLKEYLOGFILE
Linux / macOS
export SSLKEYLOGFILE=$HOME/sslkeylog.log
echo $SSLKEYLOGFILE
F5
K16700: Decrypting SSL traffic using the SSL::sessionsecret iRules command (11.6.x)
Upload the SSL KEYLOG FILE
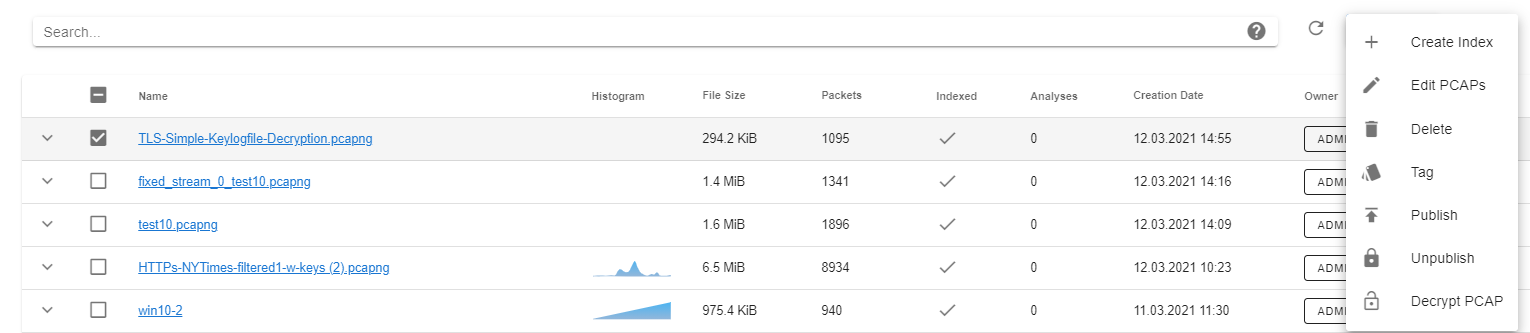
Select one PCAP in the PCAP browser and click "decrypt" in the action menu
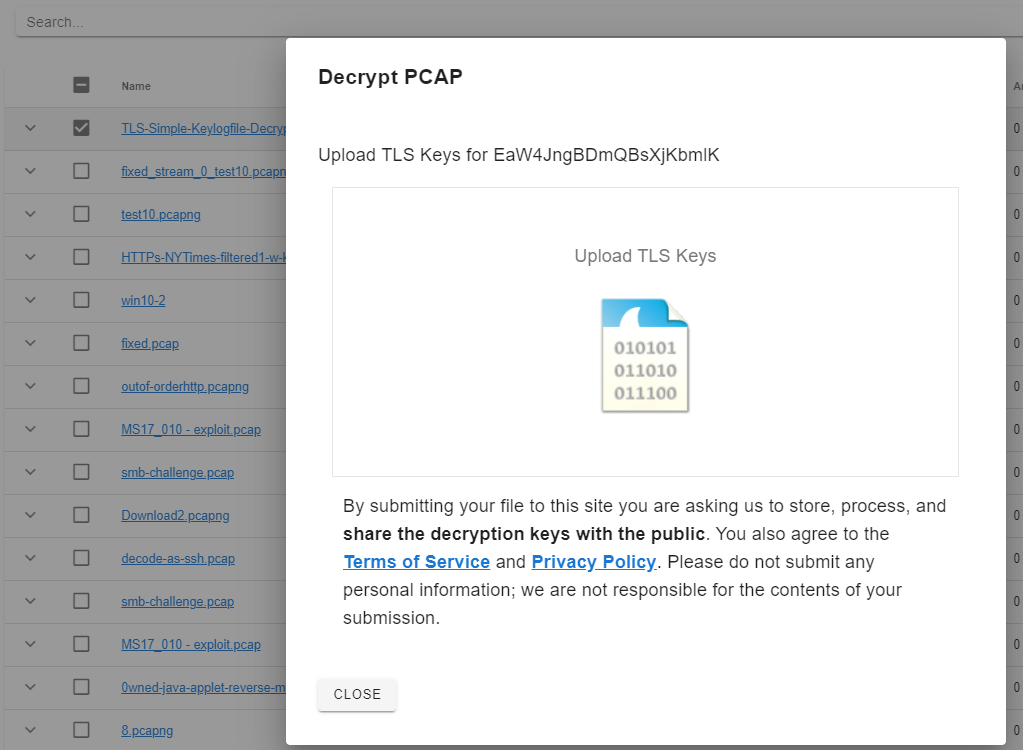
Upload the SSLKEYLOGFILE
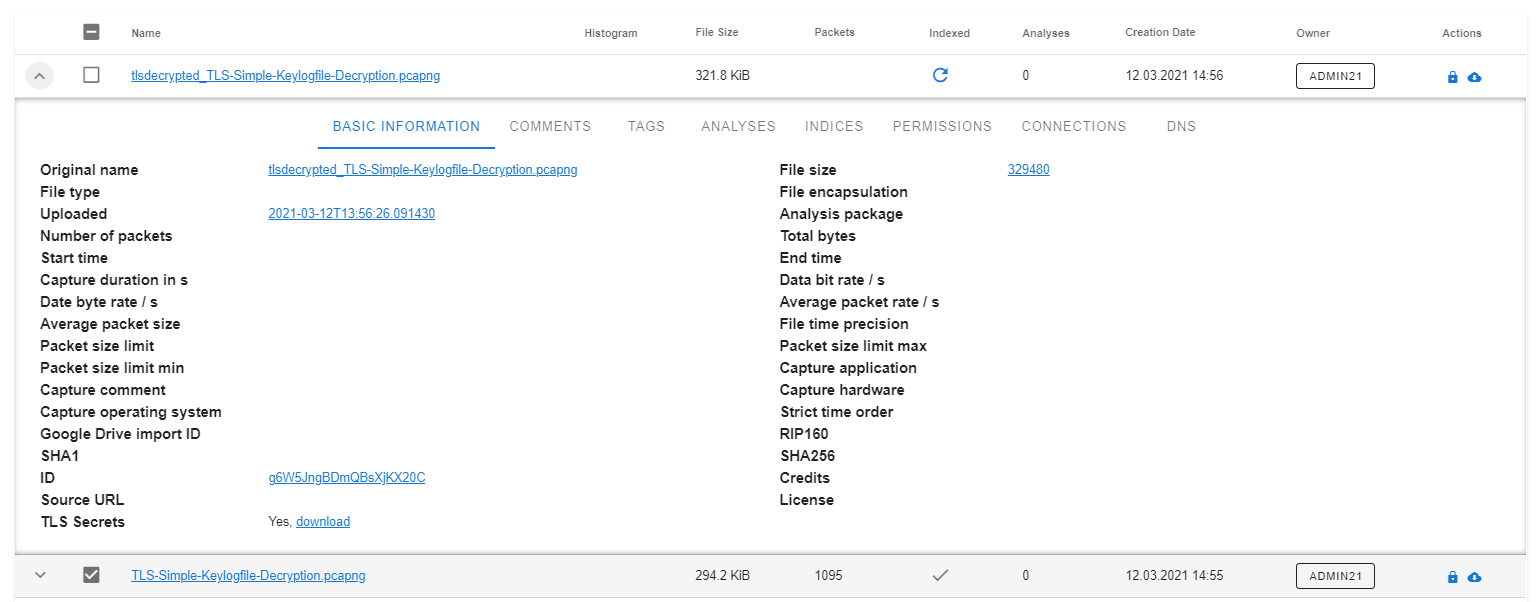
The PCAP will then show up as a newly decrypted PCAP in the PCAP browser. From here you can also download the SSLKEYLOGFILE again.
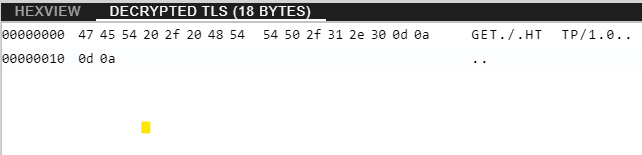
In the analysis view, you can see the decrypted packets